#Android 14 location privacy
Explore tagged Tumblr posts
Text
OS updates aren't what they used to be--which may be boring but is probably okay
I hope this post doesn't result in my having any early-adopter privileges revoked.
Procastination comes easy to me, but that usually hasn’t held up installing major operating-system updates. I typically download new mobile-OS editions within a few days of their release, while I’ve waited maybe two weeks for desktop releases despite their greater complexity and higher odds of breaking one app or another. But this season of OS updates from Apple and Google has seen me much…
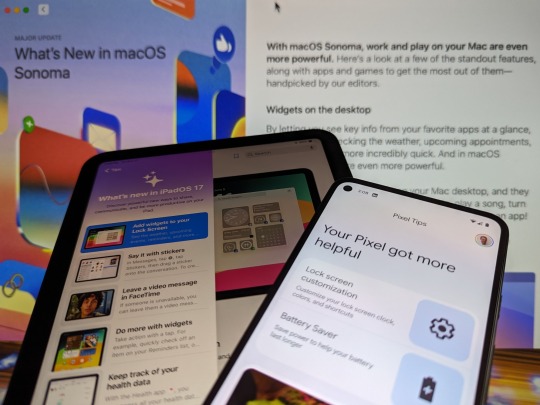
View On WordPress
#Android 14#Android 14 location privacy#iOS 17#iPadOS 17#iPadOS 17 lock screen#mac#Mac OS#Mac video reactions#macOS Sonoma#Voyager 2
1 note
·
View note
Text
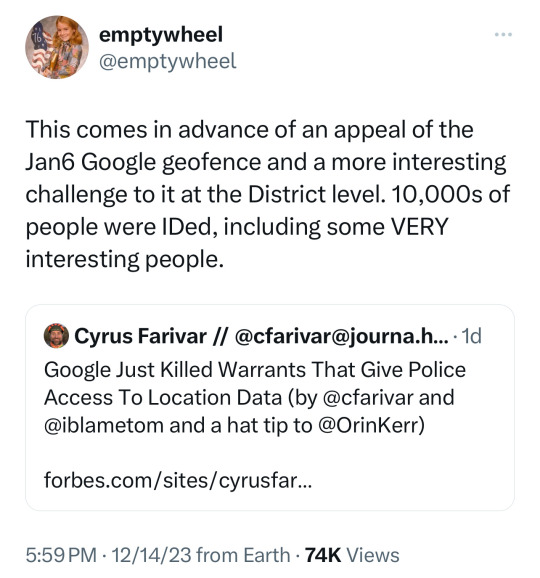
So here is the long and short of it:
Google used (uses) geofencing data, location data that undeniably shows where you and your phone have been.
Google sells this data to data brokers and advertisers, whether you like it or not. And yeah, it wouldn’t surprise me if Apple also did/does this, but if they do, Tim Cook has done a yeoman’s job of keeping it secret.
Google also hands out your location data to police departments (and governmental agencies led by conservative, anti-abortion Republicans, but I’m sure that’s unimportant, right?).
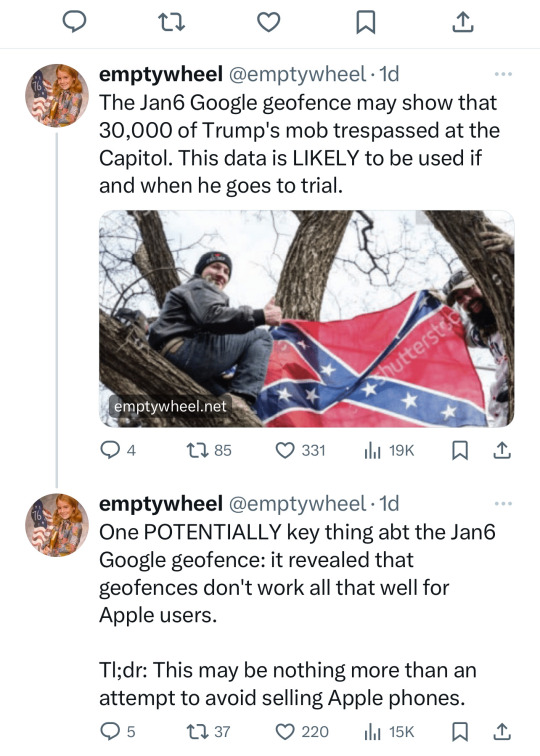
Now—and here’s the crux of the matter—just as the government was using Google’s location data to prosecute January 6th rioters, Google has had a sudden change of heart and will effectively limit their ability to remotely store your GPS information on their servers (which means it will mostly only be available locally on your Android phone’s hard drive, thus making it significantly harder - not completely impossible - for Google to give the police access to bulk location data, even if presented with a search warrant).
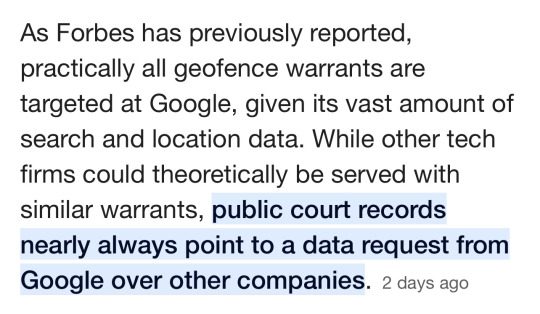
The bottom line is, it was always wrong for Google to collect and then sell their “reverse location search data” to advertisers, data miners, the police and the government. The germane question is, why now? Why has Google suddenly found Jesus, so to speak, and decided that customers privacy rights are sacrosanct, just as the U.S. government is using that data to prosecute Trump sycophants who wanted to overthrow the election?
SN: I think the whole green bubble vs. blue bubble argument is a stupid made up problem by whiny people who don’t have enough real problems in life (if you disagree then please go make your own post), and Idgaf if you’re an Android or an iPhone user. If you’re happy with your phone, that’s all that matters — but our privacy rights constantly being violated isn’t trivial, that’s actually very important. And Google suddenly deciding that now is the best time for them to end their practice of ratting people out seems highly sus.
👉🏿 https://www.emptywheel.net/2023/11/25/the-maga-tourist-geofence-and-the-violent-confederate-flag-toting-geofence/
👉🏿 https://www.forbes.com/sites/cyrusfarivar/2023/12/14/google-just-killed-geofence-warrants-police-location-data/
#politics#google#location data#privacy rights#surveillance state#geofencing#reverse location searches#andriod#android phones#j6#j6 insurrection
129 notes
·
View notes
Text
VPNs aren't just for pirates and company data anymore
A friend complained to me that they couldn't access pr0n anymore because the government is now requiring ID to verify age where they are, and due to data leaks and privacy issues, didn't want to share their ID even though they're of legal age.
Shit like this doesn't work on the intended target. It only frustrates people who are aren't tech savvy while a lot of kids have already found their way around it because that's what kids do ¯\_(ツ)_/¯
When I talk about VPNs (virtual private networks), non-tech savvy people's eyes glaze over 😂
It sounds like complicated, unknowable magic. It's not! And you don't even have to understand it to use it!
With the government and ISPs (internet service providers) invading privacy more and more and hackers breaking in and stealing user data from companies, VPNs are becoming necessary.
Some Things a VPN Does for You:
hides your data from others
can make your internet speeds faster if your ISP does speed throttling (purposely making your speed slower)
hides what you're doing from your ISP
keeps you safer from some malware, viruses, hackers, and trackers
allows you to access things that are either restricted in your area or not available in your area (such as content in other countries)
keeps you safer when you're out in public connected to wifi
Below is a basic infographic on how VPNs work. When you access the internet, a VPN encrypts your data - making it into a secret code that can't be read by anyone else including your ISP.
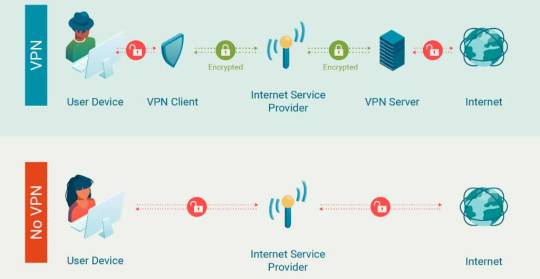
Tech companies, ISPs, etc. want you to think VPNs are complicated so that you won't use them.
When searching for a free VPN, please be aware that a lot of the free VPN services out there are malware or full of viruses and trackers.
Either do some research into which one to choose or use a paid VPN service. You can either pay monthly or yearly - the yearly is always cheaper in the long run.
Some of the Top Rated VPN Services:
ExpressVPN $7 - $13/month
NordVPN $3 - $13/month
Surfshark $2 - $14/month
PrivateInternetAccess $2 - $12/month
ProtonVPN (some sites block this one) $4 - $10/month
CyberGhost $2 - $13/month
I use ExpressVPN, so for the purposes of this post, I'm going to use screenshots from ExpressVPN.
Once you have an account, download the program from the website to your desktop/laptop or find the app on Android or iOS app stores.
Signing in requires a code that the VPN will email to you that unlocks all the features. Pay attention when the program installs because it'll ask you about preferences, and you can easily check yes on blocking pr0n when that's the reason you wanted a VPN in the first place 😂
When the program is open, you'll see this:

As you can see in the screenshot, not only do I have the program, but I have an ExpressVPN icon on my browser. The program installs this automatically, and when the program is running, the icon will have a green checkmark on it so you know it's working in your browser.
You'll notice I've recently connected using Japan. I did this so I could watch a series that isn't available outside of Japan.
The program automatically chooses a location near you, but if you want to access things that are restricted to you, make sure you click on the three dots to the right of the selected location (see screenshot below) and search for a state/country/place that your content will be available in.

Once your location is selected, click on the start/power button, and you'll get a popup notification from your computer that ExpressVPN is connected.
Go to the site you want to use and use it like you normally would.
Here's what it should look like when it's running correctly:

Keep in mind that if you leave a VPN running all the time (which is perfectly fine to do), search engines like Google will assume you live wherever ExpressVPN tells it you live, so searching for "stores near me" will give you results that aren't close to you.
When you're done using the VPN, just hit the power button again and it shuts off.
I use this on all my handheld devices, my desktop, and my laptop for business and personal reasons. I'm a pirate, and I've been using VPNs for a long time, yet none of the ISPs I've used have ever given me a warning about torrenting.
Good luck, and enjoy all the new things you can access!
BTW for anybody wondering, my desktop wallpaper is a map of the world's time zones. So pretty!! 😍
75 notes
·
View notes
Text
Genuine question-
Edit for context; my phone does and it's Android 14, with a recent update from August 1st (I didn't actually restart my phone to install it until this morning tho because I was lazy abt it.) For me it's located in settings > security and privacy > privacy > ads
16 notes
·
View notes
Text
Threads, Meta's new social media app, has signed up 100 million new users less than a week since its launch last Wednesday, making it the fastest-growing app in history.
Like other social media apps, users probably barely scanned − or skipped − the terms and conditions for what information Threads can collect, share and sell about them.
Meta probably already had a lot of information about users because Threads is built upon its Instagram platform.
Start the day smarter. Get all the news you need in your inbox each morning.
So how much does Threads already know about you, and what can it do with that data? Here are a few reasons to be concerned about your privacy.
What information does Threads collect?
Social media platforms monetize user data by selling relevant ads based on your location and activity, but, along with the usual app privacy requests like browsing history and location data, Threads also asks for financial information, health and fitness data, diagnostics and a nefarious-sounding "sensitive info."
Many users have voiced concern over Threads for its 14-point list of data permissions you're granting Meta to use the app. Twitter, by comparison, has 10 of these.
"I would say it's at the outer boundaries of what's usually expected, which is to be expected from its connection to Facebook, a brand long known for being especially hungry to take in user data and commercialize it in different ways," says Dan Ackerman, the new editor-in-chief at Gizmodo, a leading technology, science and culture news publication.
Android users can toggle off some of the data requests from the app, while the Apple App Store is "more take-it-or-leave it," Ackerman said.
"It also doesn't help that there's no browser-based fully functional version of Threads right now, and so you have to use the app version," he said.
Meta declined my request for comment and clarification.
Is Threads data collection worse than Twitter?
It's not necessarily malicious, suggests Tim Bajarin, a veteran technology analyst and Chairman of the San Jose, California-based market research firm Creative Strategies. "Users should know this Threads data list is pulled directly from Instagram, and it's all tied to their advertising engine when they start to monetize Threads.
"When you sign off on financial info, for example, they're not looking at your bank statements or anything," Bajarin said.
Rather, Threads collects what you're posting about and liking, where you are, and whether you bought something through a third-party site, app or game you logged into using your connected Facebook/Instagram ID (usually to avoid creating a new password altogether).
Bajarin said users are granting Meta access for future advertising.
"Meta isn't giving you a free app out of the goodness of their heart − they're there to make money, which is mostly from advertising."
Threads can collect and save this information, and the data can also be shared with third-party services that connect to your Threads profile.
Can you deactivate Threads?
Yes, but you cannot delete it without also deleting Instagram, Bajarin said.
"Meta built (Threads) on the Instagram infrastructure, on top of the program itself, and so it would be very difficult to uninstall one and not both – at least the way it's engineered today. ... They could eventually be spun out to be completely separate apps," Bajarin said.
To deactivate (but not delete) your Threads account, Adam Mosseri − the Instagram boss who now spearheads the Threads app – says you can choose to hide your Threads profile and content, delete individual Threads posts and set your profile to private, as reported by USA TODAY contributor Jennifer Jolly.
"Threads is powered by Instagram, so right now it's just one account, but we're looking into a way to delete your Threads account separately,” he posted.
Ackerman said the fact Threads is built on Instagram is actually a boon for Meta and users, "as it's especially easy to sign up for, has no wait list, and is simple to use." But "in order to delete your Threads account after you sign up, you’ll need to delete your Instagram account, as well, which reminds me of the difficulty people had deleting their Facebook accounts in the past, and how there was a lot of fine print about what data Facebook would keep unless you jumped through extra hoops."
Is the Threads app safe?
Threads is asking for more permissions than Twitter, so it boils down to your comfort level.
Though some of the privacy permissions seem ludicrous – granting Threads access to health and activity data and other "sensitive info" on a smartphone just seems wrong – no one is forcing users to install and use Threads or any other social media app that monetizes its free platform by delivering personalized, contextual ads to you.
Threads is available in more than 100 countries, but perhaps it's no surprise it isn't available in the Europe Union just yet: Meta was forced to pay more than $400 million by EU regulators for forcing users to accept targeted ads.
Personally, I am using and enjoying Threads quite a bit but wish there was more clarity about how my data is collected and used. And I'm disappointed Meta declined to clarify things.
I select "Ask not to track" on all iPhone apps to reduce an app's visibility into my web browsing activity, and I have a virtual private network (VPN) on my computer for extra privacy, but perhaps it's true there is nothing truly free in this world – it's just up to each person to decide whether the cost is worth it.
24 notes
·
View notes
Text
Skip to content
Simplified Privacy
Menu

Google’s Surveillance: The Shocking Truth
Google is the opposite of privacy. They maliciously collect data from you in the following ways:
The Sources for this article can be found here.
1) Saving all your Google searches, tied to your identity across devices [1] [2] [30]
2) Reading all your emails. Even if you don’t use Gmail directly, but you’re sending email to someone who does. [5] [6]

3) Saving all your web traffic if the website uses Google Ads, Captchas, or Analytics (and over 85% of all websites use some of their services). Even if you aren’t signed in to a Google account, and you’re using a VPN, they can still use past cookies and browser fingerprinting to identify you. [35] [1] [25] [26]
Google’s reCaptcha fingerprinting includes mouse movements, response time, timezone, screen dimensions, IP address, and any cookies. ReCAPTCHA uses the google.com domain instead of one specific to ReCAPTCHA, which allows Google to receive any cookies you have directly, instead of the website you’re visiting. [35] This concentrates the vast majority of all traffic data in the hands of a single company, which can then be used to de-anonymize users.
4) Everything you do in Google’s Chrome Browser is recorded, including even how long you are idle on a page. [7] [8]

5) Tracking and Saving your physical location, via Android’s GPS and Wifi triangulation. [12] [13]
Even if you turn location features off or set the phone to airplane mode, it still saves your location via Wifi triangulation, which is the process of pinging nearby Wifi hotspots to identify where you are. [9] [10] [11] Wifi triangulation can figure out your real location, even if you have a fake IP address from a VPN. [14]

As intelligence expert and ex-law enforcement Michael Bazzell says, Google is one of the first places law enforcement goes to for information because Androids track everyone’s location so accurately. Bazzell points out that even if you’re not directly involved in something, just owning an Android that was near it, can get you involved in answering police questions. Bazzell’s experience serving in law enforcement and intelligence motivated him to completely cut Google out of his life even though he’s doing “nothing wrong”. [11]
6) Keeping track of who you know to identify new phones or email accounts as you.
Rob Braxman
Privacy expert and phone operating system designer Rob Braxman points out that, by synching everyone’s phones’ contact lists and who they are physically standing near, Google (and therefore governments) can identify unknown devices or email accounts as you. [30] [31] [32a] Braxman further points to publicly available websites made by Google’s Jigsaw division and their partner Moonshot CVE, which openly sells services to governments to track and manipulate search results for targeted users. These users targeted by Jigsaw & Moonshot CVE’s government clients have their search history, location, and identifying fingerprint stored in a database. [32b]
7) Recording and saving audio of your private conversations [16] [17] [18]

Google’s Android has the microphone constantly recording and saving your intimate personal conversations against your wishes for their profit and power. As an extensive academic study of tech patents by Consumer Watch Dog points out, Google will claim this is only to find out if you said the words “Google Assistant,” but yet they have publicly filed patents to scan audio conversations and any available visuals on a variety of home smart devices to identify who is speaking, what you’re interested in, and what you’re doing for the purpose of targeted advertising. [15]

Tracking what you say, what you like, when you sleep, and even when you go the bathroom, goes well beyond Google Assistant helping you do a quick search and would instead be considered an all-inclusive surveillance. [15]
In addition, they’ll allow 3rd party apps to record you without your knowledge because of poor permissions control. As University of California Santa Barbara cybersecurity researchers presented at a BlackHat European conference, 3rd party apps like Silverpush can play high frequency audio, which is invisible to the human ear, on another device like a television ad or mall kiosk. Then your phone’s mic picks up the frequency, to rat out your real identity or location. [34]

Silverpush’s advertising system is embedded into many “free” apps on the Google Play Store. These doctoral researchers warned of the dangers this presents by being connected to wide-spread platforms like Google Ads. To demonstrate this, they played video of their lab experiment, which de-anonymatized a laptop through Tor Browser, because of an Android’s mic next to the laptop’s speakers, which was signed in to a Google account. [34]
Is the Data Sold?

Google has marketing propaganda which claims that they are merely selling advertising space on your devices and not selling the data itself. However, this claim is misleading in a number of ways.
First, not only is advertising sold by demographics or interests, but in addition, Google also allows its advertising customers to target users by name, email, or device ID and reach them almost anywhere. [1] So advertisers can target you specifically and then serve you anything on your specific device by name.

Second, while it’s true that Google technically doesn’t sell your actual name to the advertiser, when your device interacts with an ad, the third party advertiser can easily use your IP address, cross-site cookies, and/or browser fingerprinting to identify you. For example, suppose an advertiser runs an ad for an ebook on how to get out of debt. The advertiser could collect the IP addresses of anyone who clicks it, and so they’d know whose indebted.

“I think the big problem is that we give much more data to Google than it needs,” said Guillaume Chaslot, former Google engineer who worked on YouTube’s recommendations algorithm. [4a] Chaslot’s first-hand experience with Google’s spyware and manipulation inspired him to create the non-group AlgoTransparency.org, which openly says in it’s manifesto, “algorithms don’t have your best interests at mind”. [4b]
Play Store and Chrome Extensions Leak Data

Third, the Google Play Store and their Chrome Browser Extension Store leak application and user data directly to the app’s developers. This is sensitive private information, and these third party app developers are NOT carefully vetted, as almost anyone can put an app in the Google Play or Chrome Extension Store with minimal screening. Examples: [21] [23] [24]
Mental Outlaw
“Mental Outlaw” is a cybersecurity Youtube video influencer who is constantly having his videos about torrents flagged by Google as “dangerous content”. He points out how ridiculous this is because Google does so little to stop real dangerous content. One of the numerous examples he’s given is the Chrome webstore featuring extensions that are malicious hacking malware, which does URL injections to force online shoppers, without their knowledge, to use the malware creator’s affiliate links when they shop online. [22b] These 5 popular extensions got over 1.3 million downloads, which got the attention of McAfee Labs, the research department of the respected anti-virus company.

From McAfee Labs’ articulate research, this is huge security risk because not only is your personal data, like name and location, sent to malicious actors, but the attacker can forward the URL to any site they want. So you might think you’re going BestBuy.com, but it’s really the attacker’s bullshit site to get your credit card info. [22b]

Youtuber Mental Outlaw points out how ludicrous it is that not only did Google allow 1.3 million people to download these extensions, but they have featured status on the Google Chrome store. [22a] And not only does Mental Outlaw find similar malware in the Android Play Store, but Google has changed how apps disclose permissions to remove themselves of liability. Starting in mid-2022, Google has the app developers themselves disclose what permissions the app uses, so Google does not have to do any research. This is a conflict of interest, since app developers are self-reporting what information they get access to, and the end user may not properly be able to evaluate it. [19] [20a]
Sell it via Cookies

Google’s defense to these types of criticisms has always been that they don’t “sell your data” directly. But as laid out in research from the tech-savvy lawyers at the Electronic Frontier Foundation, Google allows advertisers to connect their cookies with Google’s in order to process data on the customer. This process is called “cookie matching” and essentially allows Google to sell the advertiser your information through a cookie. [1]
In the European Union, if Google were caught selling this data directly, it would be illegal. [27] [28] [29] So instead Google finds sneaky work-arounds such as the cookie matching, which allows them to appease the regulators and make statements like “we don’t sell data, we just use the data.” [1]

Conclusion

The more influence that Google has in our society, the more difficult it becomes to avoid their fingerprinting. If every website has a Google Captcha and everyone you talk to demands you talk to them on Gmail, then Google has become the gatekeeper for overseeing all human behavior. They can use this power to influence who sees your messages and what information you are able to find.

By using Gmail or Google Docs, you’re forcing and enabling Google to fingerprint your loved ones or friends. Even if you think you’re doing nothing illegal, you assume that Google will give you and those you care about an equal opportunity for your business to thrive. They can reduce Google’s search traffic to your website, or bounce your emails to potential employers or customers. They can buckle your business at the knees if they think it fits its agenda and by giving them so much information you’ve completely surrendered your freedom.
Well what is their agenda?
In our next article, we’ll discuss Google’s censorship ability to shape society and how affects you.
The Sources for this article can be found here.
Related Articles
Big Tech Abuses Medical Privacy
February 25, 2023 No Comments
In the US, your medical records are protected by HIPAA but your internet medical browsing history on websites like WebMD is NOT. That is the
Read More »
Browser Fingerprints Lead to Price Discrimination
February 25, 2023 No Comments
Some people mistakenly believe they do not need to worry about online privacy because they have “nothing to hide.” In reality, your digital identity expressed
Read More »
Avoid this Monero Vulnerability
February 25, 2023 No Comments
We love Monero. It’s our favorite and number one recommended cryptocurrency. However, it does not offer completely perfect anonymity under all circumstances because there are
Read More »
How to Reduce Google’s Control Over You
February 25, 2023 No Comments
There’s a huge number of steps you can take to reduce Google’s power and influence over your business and personal life. You would get a
Read More »
Google Censors Freedom
February 25, 2023 No Comments
This article presents evidence that Google promotes an agenda of centralized control through systematic censorship on its search, email, video, app store, and ad platforms
Read More »
Session username: Simple / Signal #: +855 68 504 905
Web 3 on IPFS: SimplifiedPrivacy.x
Tor Onion: privacypkybrxebcjicfhgwsb3coatqechwnc5xow4udxwa6jemylmyd.onion
Nostr Public Key: npub14slk4lshtylkrqg9z0dvng09gn58h88frvnax7uga3v0h25szj4qzjt5d6
[email protected] / @Matrix:SimplifiedPrivacy.is
14 notes
·
View notes
Text
Subkuz - The World's First Location-Based, Multilingual News Portal
🌏 Introduction:
Subkuz.com is not just a news portal—it's a groundbreaking information revolution. A cutting-edge platform that bridges communities, honors linguistic diversity, and harnesses advanced technology to deliver trustworthy, relevant, and customized content to the Indian diaspora and residents in their native languages.
🔹 World’s First: Location-Based, Multilingual News Portal 🔹 14 Indian Languages | 200+ Cities | Hyper-Local to Global Coverage 🔹 Fresh, Authentic, User-Friendly Content
Subkuz.com’s Purpose: To empower every Indian globally with accurate, unbiased, and reliable information in their preferred language, fostering deeper connections to their society, culture, and community.
🚀 Foundation & Vision:
Subkuz.com was founded with a clear vision: "Democratizing information and eliminating language barriers."
Our mission is to connect Indians not just with India, but with local activities, community updates, and administrative information from wherever they reside globally, all in their mother tongue.
⭐ Key Features of Subkuz.com:
📍 1. Location-Based Smart Algorithm:
Real-time, customized news delivery based on each user’s city, country, and interests—covering hyper-local to global levels.
🗣️ 2. Content in 14 Indian Languages:
Premium content available in Hindi, Marathi, Tamil, Telugu, Bengali, Kannada, Gujarati, Punjabi, Malayalam, Odia, Assamese, Bhojpuri, Dogri, and Maithili.
🌐 3. Live Network in 200+ Cities:
A vast reporting network spanning over 200 cities globally, delivering fresh, ground-level, authentic news.
📱 4. Fresh & User-Friendly App Experience:
iOS and Android apps offer personalized, fast, and data-privacy compliant user interfaces.
🌏 5. Diaspora-Centric Sections:
Embassy announcements, local events, and administrative updates specially curated for the Indian diaspora.
✍️ 6. Global Platform for Content Creators:
Independent journalists, bloggers, and local writers can amplify their city, society, and community voices.
Submissions: [email protected]
🎯 Subkuz.com’s Mission & Approach:
Vision: "Delivering empowering, unbiased, and authentic information to every Indian in their language."
Mission:
Breaking linguistic and geographical barriers
Deeply connecting Indian diaspora with local societies and cultures
Preserving Indian cultural and social values
Strengthening global social dialogue and unity
🛠️ Technological Excellence of Subkuz.com:
Location-Based Algorithm: Customized news feed
AI-Enabled Personalization: Smart content suggestions
Data Privacy & Security: Compliance with GDPR, Indian IT regulations, and top-tier data security standards
1 note
·
View note
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product Description Use VPN to protect your identity and secure your data Safehouse VPN hides your location and encrypts your data, keeping you safe from small crooks and big tech. It also lets you access geo-blocked content and use public Wi-Fi safely. Click with confidence with Safehouse Do you ever worry you’ll accidentally click on a dangerous link? With link protection in Safehouse, you can click with confidence. We scan and filter every link you click, and warn you against opening phishing, scams or fraud. We also prevent you from entering websites with malware. Cyber Insurance to keep you protected from any unauthorised digital transactions Rs 25,000 cover by HDFC ERGO for any unauthorised digital transactions from your bank account, digital wallets, cards, UPI. Available only for Indian citizens. Track your lost or stolen phone in just minutes If your phone is lost or stolen, you can lock it remotely and secure your data. If you think your phone was stolen, play a loud siren remotely and snap a picture of the person trying to access your data. Safety Score keeps you informed and in control of your safety Find out, at a glance, how exposed you are to digital threats, and follow simple steps to monitor, control and improve your online safety. Compatible with both Android (version 10 and above) and Apple IOS (14 or above Version) Smart phones and tablets. Global VPN - Protect your device privacy, hide your IP address, secure your connection on public Wi-Fi Unlock Content: Enjoy the sites and apps blocked by your ISP/Wi-Fi provider with our high speed VPN servers. Active Defence - Block pop-ups, unsafe content on sites and websites that serve malware, phishing or viruses. Cyber Insurance: Rs 25,000 cover by HDFC ERGO for any unauthorised digital transactions from your bank account, digital wallets, cards, UPI. Available only for Indian citizens. Link Protection - Detect and block access to scam or malicious websites before you accidentally open them. Remote Control - Locate your phone if it is ever lost or stolen. You can remotely lock your phone, track its location, play a loud siren, take a snapshot of the thief who tries to access your device. Breach Detection - Check if your email address has been a part of a data breach in the past and if so, recommendations to mitigate the security risks. [ad_2]
0 notes
Text
Troop Messenger vs Telegram: Why You Should Consider Switching
Are you looking for Telegram alternatives? Then read this blog to discover alternative messaging platforms and get a quick overview.
Troop Messenger
Since Telegram is used by a few start-ups and small enterprises, I figured Troop Messenger and others could be added to the list. Troop Messenger is undeniably more than a Telegram alternative. Troop Messenger offers a lot of features compared to Telegram, which is far superior in terms of providing quality. For instance, Troop Messenger groups will have great advantages compared to Telegram chatting groups such as admin super controls, advanced search filters, screen sharing within group calling, and so on.
One of the encrypted chat programs on the list is Troop Messenger, and it's possible that you've already used the safest one. Due to its superior security features, political parties utilise it as their political campaign software, and the defence agencies of a few strong nations employ it for defence collaboration services. You can therefore gauge the tool's security. There aren't many products like Troop Messenger available on the market that can be supplied via all of the main delivery models, including chat APIs and SDKs, on-premise, SaaS, etc.

Apart from chat basic functions, Troop Messenger is a complete team collaboration tool that provides its users with all the features such as audio/video conference, screen sharing, remote access, live location tracking, and so on.
Do you know that Troop Messenger has a Burnout feature similar to Telegram’s secret chat? Teams, Defense agencies, and government officials can use it to convey classified information that no one else on the planet, including service providers, has access to.
Telegram is a cloud-based instant messaging software that is freeware and cross-platform. End-to-end encrypted video calling, file sharing, VoIP, and other functions are also available. Telegram's initial release date was August 14, 2013, for iOS and October 2013 for Android.
Nikolai and Pavel Durov, who were also the inventors of the Russian online social site RK, launched Telegram in 2013.
Telegram's data is dispersed over five data centers in various locations around the world, including the operations center in Dubai, United Arab Emirates.
After WhatsApp announced its privacy policy in January 2021, 25 million new users joined Telegram, according to Telegram creator Pavel Durov. This equates to almost 8.33 million new users signing up every day. Telegram added over 100 million new users in just the month of January.
Telegram quickly made a name for itself as a competitive WhatsApp substitute. A few publications claim that Telegram currently has over 550 million active members and ranks in the top 10 most popular social networks globally in terms of download volume. Businesses were compelled by Telegram's popularity to get their app developers to produce an ideal substitute.
Why is Telegram not recommended?
Even though a few companies use it, Telegram shouldn't be on your list of chat apps for your team or place of business. It wouldn't meet all workplace requirements because it's a social messenger unless you wanted to limit it to phone calls, conversations, and file sharing. Telegram will merely function as an additional messenger, similar to FaceTime, WhatsApp, and the like. Nevertheless, a strong team communication tool can enhance teamwork and increase productivity at work, something that Telegram apps are unable to accomplish.
Check Point issued a Telegram warning in 2021, that "it tracked 130 cyber attacks that used malware managed over Telegram by attackers. Even though Telegram is not installed or being used, it allows hackers to send malicious commands and operations remotely via the instant messaging app."
What are the disadvantages of Telegram?
Here are some of Telegram's drawbacks that may make you want to uninstall it and look out for Telegram alternatives.
Telegram collects users’ contact details and metadata
If the articles are to be believed, Telegram is not an end-to-end encrypted
It has limited support
Since Telegram has a 1.5 GB file size limit, illegally downloaded movies are being mixed in with adult content that is not appropriate for children.
Telegram also allows attackers to access hacked machines from practically anywhere on the planet using their mobile devices.
Due to some operational advantages, cybercriminals are increasingly using Telegram as part of their activities.
Attackers can simply exfiltrate data from victims' PCs or transfer new malicious files to infected machines owing to Telegram's unique communication features.
Observing the above-mentioned segmentations, on the contrary, users have huge benefits from utilizing Telegram as their social chat app, which any app like Telegram may not offer.
If you believe that we are being subjectively biased by pointing out Telegram's drawbacks, further information will show just how objective we are.
How have users benefited from Telegram?
Do you know that with 700 million monthly active users, Telegram has ascended to become one of the top 5 downloaded apps globally in 2022? According to Telegram, it has never spent money on advertisements; instead, it was users who shared their positive experiences with other users (friends, relatives, acquaintances, colleagues, and others). As a result, they were persuaded to download it.
In light of this, Telegram introduced a premium plan that gives users access to extra premium features while allowing free use.
Telegram Premium
Users will have access to increased limits, better chat management, 4 GB file uploads, faster downloads, exclusive stickers and reactions, and other benefits with Telegram Premium. Despite this, non-premium users will still have access to all current capabilities. In fact, they may even be granted access to select privileges, such as
Ability to download large documents.
Tap to increase the counts on premium reactions that have already been added to a message.
Can view the stickers that Premium users have sent.
Some of the enticing features that premium users can access are
1. Chat Management
New tools in Telegram Premium help you organize your conversation list, such as setting your default chat folder to ensure that the app always starts on Unread instead of All Chats.
Indeed, subscribers can keep the busiest chat lists organized by enabling a Privacy and Security feature that automatically archives and mutes new chats.
2. Animated Profile Pictures
Everyone using the app can see the animated profile videos of premium users in chats and the chat list. In addition, premium users can demonstrate their fresh look to the world or showcase their creativity with a unique looping animation.
3. 4GB Uploads
Those who use Telegram Premium can now send files up to 4 GB in size, which provides sufficient space for 4 hours of 1080p video or 18 days of high-quality audio. At the same time, non-premium users can indeed upload files and media up to 2 GB in size and take advantage of unlimited free storage in the Telegram Cloud.
4. Faster Downloads
Media and files can be downloaded as quickly as possible for premium subscribers. Users get limitless access to their cloud storage and can access everything as quickly as their network can accommodate.
5. Doubled Limits
Doubled limitations are available to premium users for everything in the app, including:
Can add the fourth account,
Able to follow 1000 channels,
Create up to 20 chat folders, each containing a maximum of 200 chats,
Add ten chats to the main list,
Ten favorite stickers may be saved,
Ability to write a longer bio and add a link to it.
6. Voice-To-Text
For those occasions when you cannot listen but still wish to see what it says, voice messages can be converted to text. You can give transcriptions a rating to help them get better.
7. Unique Stickers
There are dozens of stickers available for Premium users to send in any chat to add extra emotion and expressive effects to engage the recipients while still making them visible to all users. These stickers are meant to impress, especially millennials, and feature full-screen animations. In contrast to Telegram alternatives, the Telegram team of artists will update a premium sticker collection every month.
8. Premium Badges
In the chat list, chat headers, and member lists in groups, all premium users have a special badge that says "Premium" next to their names, signifying that they are a member of the club that gets first access to unique features.
9. Premium App Icons
Premium customers have the option to add new icons to their Home Screen in an attempt to make it more compatible with their personality or wallpaper.
Telegram guarantees its users that it will continue to implement free features that are accessible to everyone and that it will do it more quickly than any other app similar to Telegram.
Conclusion
If the encryption is disregarded, Telegram can serve as a popular social media chat software, but it is a terrible tool for team and corporate interactions. Whereas hackers are using Telegram data to their advantage, WhatsApp is only gathering commercial data from particular companies. Telegram needs to start prioritising security, or else users will begin to migrate to other messaging apps.
0 notes
Text
Cricut Explore Software Download: Quick and Easy Guide
Hey, Cricut users! Are you here to learn about the Cricut Explore software download? If so, I’ve got your back! Downloading and installing the Cricut Design Space software on various computers and operating systems is a difficult task. But I think this is only the case for beginners. Hence, they need a simple guide to understand so that they can download the app on their compatible devices. I am here to teach the same method to beginner Cricut users.
However, users need to remember one thing before downloading the Cricut software on their devices. These are the system requirements, which I have explained briefly. As an experienced crater, I will teach you how to download the Cricut app on Windows, Mac, Android, and iOS. Let’s get started!
Cricut Explore Software Download on a Windows Computer
You can download the Cricut software hassle-free on Windows. The compatible computer to run the Cricut Design app on your Windows computer is Windows 10 or later. You will also need an Intel Dual Core or equivalent AMD CPU with 4 GB of RAM. If your system meets these requirements, you are ready to download the app.
Here is how to download the Cricut app on your Windows PC:
Power on the computer device.
Then, you need to launch an internet browser.
Now, you have to copy & paste the URL design.cricut.com on the search bar.

4. After that, you need to click on the checkbox to agree to Cricut’s Terms of Use and Privacy Policy.
5. Then, hit on the Download tab.
6. When it is downloading your software, you might notice some changes to your screen. These changes may vary for every browser.
7. Once your file has been downloaded, move it to the Downloads folder from the File Explorer.
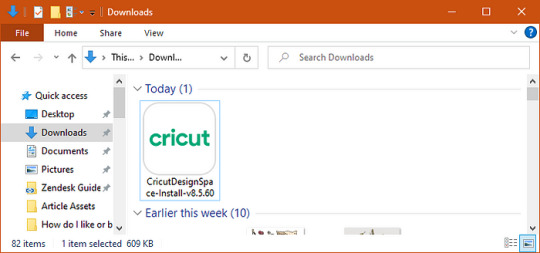
9. Next, select Yes to allow your app to make some changes to your PC.
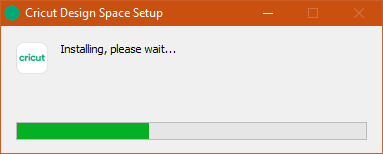
11. Finally, your Cricut Design Space software is downloaded.
Cricut Explore Software Download on Your Mac Computer
To download Cricut software on a Mac, you need to know the system requirements, such as macOS 11 or later. Make sure you have a 1.83 GHz CPU and 2 GB of free disk space. When these requirements are met, it will be easier to run the Cricut Design app smoothly.
Here is how to download the Cricut software on Mac:
In the beginning, start your MacBook.
Launch an internet browser you use on it (I am using Google Chrome here).
After that, you have to go to the browsers.
Navigate to the browser’s search bar and type design.cricut.com.
Then, check the checkbox to accept Cricut’s Terms of Use and Privacy Policy.
Next, you should select the Download button.
Move to a page where you need to choose the file location. This is where you will download your file.
Finally, your downloading starts from here.

9. Once the download is complete, move to the Downloads folder.
10. After that, you will see a .dmg file in your Downloads folder.
11. Then, you will notice the .dmg file; double-click on it to start the installation.

Cricut Explore Software Download on Your Android Mobile
Android users need to have Android 10.0 or higher. The Cricut software is also compatible with mobile devices and tablets. Despite this, you can easily download the app if you have a 2 to 3 Mbps download and upload speed.
Here is how to download the Cricut app on Android phones:
11. On your Android phone, go to your home screen.

13. Then, you have to type Cricut Design Space on the search bar.
11. Next, in the below result, you will find a Cricut software icon.
12. Click on the app icon.

14. Once you have installed it, you can find this app on your home screen.
Cricut Explore Software Download on an iOS Device
Being an iOS user, I always use my Cricut app on the latest device. However, according to Cricut, iOS 15 or later is recommended. If you have 2–3 Mbps download and upload internet speed, you are good to go!
Here is how to download the Cricut software on iOS smartphones.
On iPhone or iPad devices, launch the App Store.

2. Then, head to the search bar and type Cricut Design Space.
3. Now, you will see a Cricut Design app.

6. Finally, you can start setting it up smoothly.
FAQs
Question 1: What is Cricut software for desktops?
Answer: The Cricut software is editing or designing software for Cricut users that supports Windows and Mac hassle-free. It is a companion app that runs the Cricut machine. This software is initially required to set up the Cricut. The software is also a platform for creating amazing craft designs easily and quickly. It offers free resources, including images, ready-made resources, and much more.
Question 2: How can I use Cricut Design Space without the internet?
Answer: Except for downloading software, you can use the Cricut machine to work offline anytime. While being offline, the internet is not required, and hence, you can create any designs easily and quickly. However, you might need the internet when you want to save your project or access some online resources.
Question 3: Can you use Cricut without a computer?
Answer: No, you cannot! Actually, without a computer or mobile device, you can’t use a Cricut machine. However, the machine is run with the help of companion software, which is downloaded to your computer and mobile app. To run this app, you need either a computer or a phone. In short, you can’t use a Cricut machine without a computer.
Source: cricut explore software download
Visit here For More Information: Cricut.com/setup
You tube
#cricut explore software download#download cricut software#cricut design space software#Cricut Explore Air 2#Cricut.com/setup
0 notes
Text
Taxi Booking App Development: New Travels Booking Ideas
Taxi Booking App Development: Revolutionizing Transportation
Introduction
The advent of smartphones and the rapid growth of the on-demand economy have transformed the way we commute. Gone are the days of hailing a taxi on the street or waiting at a taxi stand for your turn. Today, we rely on taxi booking apps to conveniently and efficiently get from point A to point B. In this 2000-word guide, we will delve deep into the world of taxi booking app development, exploring the process, essential features, challenges, market trends, and the promising future of this industry.
I. The Taxi Booking App Ecosystem
Before we dive into the development process, let's understand the ecosystem of taxi booking apps:
Passenger: The end-users who book rides through the app.
Driver: Individuals who provide transportation services and use the app to receive ride requests.
Admin: The app's administrator who manages the platform, sets rules, and monitors operations.
Dispatcher: Optional, but sometimes essential for large fleets. Dispatchers manage ride allocation to drivers.
II. The Development Process
Developing a taxi booking app involves several key stages:
1. Idea Validation and Market Research
Understand the target market and its specific needs.
Research the competition and identify gaps in the market.
Validate your app concept with surveys, focus groups, or beta testers.
2. Design and Prototyping
Create wireframes and prototypes to visualize the app's flow.
Design a user-friendly and intuitive interface for both passengers and drivers.
Pay attention to UX (User Experience) to ensure easy navigation and usage.
3. Technology Stack Selection
Choose the development platform (iOS, Android, or cross-platform).
Select the appropriate technology stack, including programming languages and frameworks.
4. Backend Development
Build the server-side components to handle user data, requests, and communications.
Implement essential features such as user registration, authentication, and payment processing.
5. Frontend Development
Develop the passenger and driver apps with real-time GPS tracking, ride booking, and notifications.
Ensure a seamless user experience across different devices.
6. Integration of GPS and Maps
Utilize map APIs like Google Maps or Mapbox for real-time location tracking and route optimization.
7. Payment Gateway Integration
Integrate secure payment gateways to facilitate transactions.
Ensure compliance with payment industry standards (PCI DSS).
8. User Authentication and Verification
Implement robust security measures for user authentication and data protection.
Verify user identities for safety and trustworthiness.
9. Ratings and Feedback System
Include a system for passengers and drivers to rate and provide feedback on each other.
Use this data to improve service quality.
10. Testing and Quality Assurance
Thoroughly test the app for functionality, security, and performance.
Fix any bugs or issues that arise during testing.
11. Launch and Marketing
Publish the app on app stores (iOS App Store and Google Play Store).
Create a marketing strategy to promote your app, including online advertising, social media, and partnerships.
12. Driver Onboarding
Recruit drivers and provide training on using the app.
Verify driver licenses, backgrounds, and vehicle information.
13. Legal and Regulatory Compliance
Ensure compliance with local transportation regulations, data privacy laws, and taxation requirements.
14. Maintenance and Updates
Regularly update the app to fix bugs, add new features, and improve performance.
Address user feedback and suggestions.
15. Customer Support
Provide channels for users to report issues and seek assistance.
Offer prompt customer support to enhance user satisfaction.
16. Analytics and Data Insights
Implement analytics tools to track user behavior, app performance, and business metrics.
Use data insights to make informed decisions.
III. Key Features of a Taxi Booking App
A successful taxi booking app should include a range of essential features to meet the needs of both passengers and drivers:
For Passengers:
User Registration and Profile Management: Allow passengers to create and manage their accounts.
Location-Based Services: Enable users to enter their pickup and drop-off locations easily.
Real-Time Vehicle Tracking: Show passengers the real-time location of their assigned driver.
Ride Booking: Let passengers book rides with options like vehicle type, fare estimates, and ride scheduling.
Payment Integration: Integrate secure payment gateways to process transactions and offer multiple payment methods.
Notifications: Send notifications about ride updates, promotions, and payment receipts.
Ratings and Reviews: Allow passengers to rate drivers and provide feedback on their experiences.
History and Ride Records: Show passengers their ride history and transaction records.
Support and Help Center: Provide customer support channels and FAQs.
For Drivers:
Driver Registration: Enable drivers to sign up and submit required documents.
Driver Dashboard: Provide a dashboard to manage ride requests, earnings, and schedules.
Accept/Reject Rides: Allow drivers to accept or reject ride requests.
GPS Navigation: Integrate GPS navigation to help drivers reach passengers and destinations efficiently.
Earnings and Reports: Show drivers their earnings, trip reports, and payment details.
Messaging and Communication: Allow drivers to communicate with passengers via in-app messaging.
Driver Ratings: Display driver ratings and feedback from passengers.
Support and Help: Offer support and assistance channels for drivers.
Admin Panel:
User and Driver Management: Manage user and driver accounts and profiles.
Dispatch System (optional): If applicable, allocate rides to drivers.
Fare Management: Set and manage pricing and commissions.
Analytics and Reporting: Monitor app performance, user behavior, and financial data.
Emergency Features: Implement safety features, such as an SOS button or emergency contact.
IV. Challenges in Taxi Booking App Development
Building a taxi booking app comes with its own set of challenges:
Competition: The market is highly competitive, with established players like Uber and Lyft.
Regulatory Compliance: Adhering to local transportation regulations can be complex and costly.
Security and Privacy: Ensuring the safety of both passengers and drivers' personal information is crucial.
User Trust: Building trust is vital, as passengers trust drivers with their safety and drivers trust the platform with their income.
Driver Onboarding: Recruiting and onboarding drivers while maintaining quality can be challenging.
Scalability: As the user base grows, the app must be scalable to handle increased traffic.
V. Market Trends and Opportunities
The taxi booking app industry continues to evolve with emerging trends and opportunities:
Electric and Autonomous Vehicles: The shift towards electric and autonomous vehicles is influencing the industry.
Sustainability: More users prefer eco-friendly transportation options, leading to a rise in electric and hybrid vehicles.
Multi-Modal Transportation: Apps are integrating various transportation modes like bikes, scooters, and public transit to offer comprehensive solutions.
Micro-Mobility: The popularity of shared bikes and scooters is on the rise.
Personalization: Apps are increasingly using AI and data analytics to offer personalized experiences.
Delivery Services: Expanding into delivery services for food, groceries, and packages presents new revenue streams.
VI. The Promising Future of Taxi Booking Apps
The future of taxi booking apps looks promising, driven by technological advancements and changing user preferences:
Electric and Autonomous Fleets: Electric and autonomous vehicles are expected to become more common, reducing operating costs and environmental impact.
Enhanced Safety Measures: Continued focus on safety features, including real-time monitoring and emergency response systems.
Market Expansion: Expanding into underserved regions and markets presents growth opportunities.
Integration with Smart Cities: Collaboration with smart city initiatives for efficient urban mobility.
Sustainability: Sustainability and environmental concerns will continue to shape the industry.
Mergers and Acquisitions: Ongoing consolidation and partnerships within the industry.
Native Development For Android $ 8,500 For iOS $ 9,000
UI/UX Design For Android $ 3,000 For iOS $ 3,500
Backend Development For Android $ 4,000 For iOS $ 4,500
Admin Panel Development For Android $ 3,100 For iOS $ 4,100
Quality Assurance For Android $ 5,500 For iOS $ 6,800
Project Management For Android $ 3,000 For iOS $ 2,600
Total For Android $ 27,100 For iOS $ 30,500
Conclusion
The development of a taxi booking app is a complex journey that involves a deep understanding of user needs, technical expertise, and adherence to regulations. However, with the right strategy, a robust feature set, and a commitment to quality, a taxi booking app can become a valuable asset in the evolving world of transportation.
The future holds immense potential for taxi booking apps, with advancements in technology, sustainability, and user experience poised to drive innovation and growth in this dynamic industry. As users continue to seek convenient and efficient transportation solutions, taxi booking apps are likely to play an increasingly significant role in shaping the future of urban mobility.
US-based developers charge $160-$300/per hour Eastern-Western developers charge $60-$200/hour India-based developers charge $8-$50/hour
#taxibookingappindia#androidappdevelopment#iosappdevelopment#howtodeveloptaxiapp#Howmuchdoesitcosttodevelopataxiapp?
0 notes
Text
Best Grocery app development company in Greater Noida|Best app development in Greater Noida|Grocery app development company in Greater Noida|Grocery app development company in Mumbai| Top 5 Grocery app development company in Greater Noida|Best catalog designer in Greater Noida|Browser catalog design in GREATER NOIDA| Best catalog Designer in Greater Noida

Developing a grocery app requires careful planning, a user-centric approach, and attention to various technical aspects. Here are the steps and considerations for creating the best grocery app:
1. Market Research:
Understand your target audience and their needs.
Research competitors and identify gaps or opportunities.
2. Define Your Unique Selling Proposition (USP):
Determine what sets your grocery app apart from others.
Identify the key features or benefits that will attract users.
3. Choose a Business Model:
Decide whether you'll sell groceries directly, partner with local stores, or use a hybrid approach.
Explore revenue streams such as delivery fees, subscription models, or advertising.
4. Develop a Business Plan:
Outline your app's objectives, budget, and revenue projections.
Define your marketing and growth strategies.
5. Technical Requirements:
Select a platform (iOS, Android, or both) for app development.
Choose the technology stack (programming languages, frameworks) based on your development team's expertise.
6. Design User-Friendly UI/UX:
Create an intuitive and visually appealing user interface (UI).
Ensure smooth user experience (UX) with easy navigation and minimal friction.
7. Core Features:
Registration and User Profiles
Product Listings and Search
Shopping Cart and Checkout
Payment Integration
Order Tracking
Push Notifications
Reviews and Ratings
Discounts and Promotions
Customer Support
8. Backend Development:
Develop a robust backend system to manage product listings, inventory, user data, and orders.
Implement security measures to protect user data and transactions.
9. Integration with Third-Party Services:
Integrate payment gateways for secure transactions.
Implement geolocation services for location-based features.
Partner with local grocery stores for inventory data.
10. Testing: - Conduct thorough testing, including functional, usability, and security testing. - Fix any bugs or issues that arise during testing.
11. Launch: - Submit your app to the respective app stores (Google Play Store and Apple App Store). - Promote the launch through various marketing channels.
12. Post-Launch Optimization: - Gather user feedback and make improvements based on their suggestions. - Monitor app performance and resolve any issues promptly. - Continuously update the app with new features and improvements.
13. Marketing and User Acquisition: - Implement a marketing strategy to attract users. - Consider running promotions, referral programs, or partnerships with local businesses.
14. Customer Support: - Offer excellent customer support through in-app chat, email, or phone. - Address user concerns and issues promptly.
15. Data Analytics: - Implement analytics tools to track user behavior and gather insights. - Use data to make informed decisions and improve user engagement.
16. Legal and Compliance: - Ensure that your app complies with data privacy regulations (e.g., GDPR). - Protect your business with proper legal agreements and terms of service.
17. Scaling: - Plan for scalability as your user base grows. - Consider expanding to new regions or adding additional features.
Developing the best grocery app requires a holistic approach that encompasses both technical and user-oriented aspects. Keep the user experience at the forefront, continuously improve your app based on user feedback, and adapt to changing market conditions to succeed in the competitive grocery app industry.
#Best Grocery app development company in Greater Noida#Best app development in Greater Noida#Grocery app development company in Greater Noida#Grocery app development company in Mumbai#Top 5 Grocery app development company in Greater Noida#Best catalog designer in Greater Noida#Browser catalog design in GREATER NOIDA#Best catalog Designer in Greater Noida
0 notes
Text
How to Find the Best VPN for Torrenting Reddit
The best VPN for torrenting Reddit, if you find yourself overwhelmed by the sheer number of options to choose from. Torrenting can be described as popular recreation among Reddit visitors, who sometimes share not to mention download file types from a number of sources. But, torrenting may well expose want you to many negative aspects, such for the reason that malware, copyright infringement, ISP throttling, not to mention legal inconveniences.
That's why you need a VPN to shield your personal space and security measure while torrenting. Some VPN, and / or virtual privately owned network, encrypts your web traffic not to mention hides a IP treat from neighbor's eyes. In such a manner, you are able to torrent anonymously not to mention safely, without disturbing about a ISP or everyone else tracking your online activity.
How to find typically the best VPN for torrenting Reddit?
Except for all VPNs are acceptable for torrenting. Numerous VPNs need slow gears, weak encryption, or dripping connections that might compromise a torrenting past experiences. Others need strict regulations that restrict or limitation torrenting on their servers. Many VPNs are actually downright shady which enable it to log your computer data or offer for sale it towards third occasions.
Here are actually some things to consider:
Speed: You want a VPN that fast not to mention consistent gears for consistent torrenting. An outstanding VPN requires a good sized network from servers in different locations, allowing you to always consider a server who suits your company needs. You ought to seek for a VPN who supports P2P potential customers on virtually all or much of its staff, and is without bandwidth hats or throttling.
Security measure: You choose a VPN who uses effective encryption not to mention protocols towards secure your computer data and stay away from leaks. An outstanding VPN requires features for a kill convert, DNS leak protection, and divided up tunneling to your security measure and personal space. You ought to seek for a VPN which has had a strict no-logs policy as well as based in any privacy-friendly legislation.
Compatibility: You want a VPN that is effective with a devices not to mention platforms. An outstanding VPN requires apps for the purpose of Windows, Macintosh, Android, iOS, and various other popular systems. You ought to seek for a VPN who supports different simultaneous associates, so you can actually protect every one of your devices without delay.
Customer program: You choose a VPN that reliable not to mention responsive customer care. A fantastic VPN requires a exist chat have, a wide-ranging FAQ spot, and some helpful program team to guide you with any sort of issues and / or questions. It's advisable to look on a VPN which has had a money-back guarantee maybe a free litigation, so you can look at it through before giving.
Best VPN for Torrenting Reddit
The best VPNs for the purpose of torrenting Reddit might be CoverMeVPN. CoverMeVPN can be described as fast, protect, and user-friendly VPN that all you need for torrenting. Listed below are some of reasons why CoverMeVPN is better choice for the purpose of torrenting Reddit:
CoverMeVPN seems to have over 3000 staff in 94 cities, so you can actually always consider a server who meets a speed not to mention location selections. CoverMeVPN aids P2P potential customers on virtually all its staff, and seems to have unlimited bandwidth rarely are throttling.
CoverMeVPN takes advantage of AES-256 encryption not to mention OpenVPN protocol to shield your data files from criminals and snoopers. CoverMeVPN can also have a ruin switch, DNS leak protection, divided up tunneling, and various other advanced features to your security measure and personal space.
CoverMeVPN 's coming a stern no-logs policy as well as based in your British Virgin Islands, that may be outside typically the 14 Big eyes alliance.
CoverMeVPN seems to have apps for the purpose of Windows, Macintosh, Android, iOS, Linux, routers, and others. CoverMeVPN allows roughly 5 simultaneous associates per profile, so you can actually protect every one of your devices without delay.
CoverMeVPN possesses a 24/7 exist chat program, an broad FAQ spot, and a genial support team which enables you with the help of any factors or thoughts. CoverMeVPN can also have a 30-day money-back guarantee and then a 7-day sample of, so you can test it through risk-free.
CoverMeVPN will be best VPN for torrenting Reddit mainly because it offers easily speeds, effective security, convenient compatibility, and excellent customer care. With CoverMeVPN, you can actually torrent anonymously not to mention safely concerning Reddit free of compromising a privacy and / or performance.
Conclusion
Subsequently, finding typically the best VPN for torrenting Reddit is absolutely not a hassle-free task. There are a lot factors to look at, such for the reason that speed, security measure, privacy, compatibility, not to mention cost. But, by using the tips not to mention recommendations through this blog put up, you are able to narrow down your alternatives and pick out a VPN who suits your company needs and selections. By finding a VPN for the purpose of torrenting Reddit, you are able to enjoy can online anonymity, security measure, and escape. You are able to access geo-restricted articles and other content, bypass censorship, and prevent ISP throttling. You too can share not to mention download file types with various Reddit visitors without disturbing about legal issues or cyber threats. A VPN can be described as must-have tool for your torrenting buff who figures online personal space and defense.
If most people check his or her's reviews, explore CoverMeVPN.
0 notes
Text
Skip to content
Simplified Privacy
Menu

Google’s Surveillance: The Shocking Truth
Google is the opposite of privacy. They maliciously collect data from you in the following ways:
The Sources for this article can be found here.
1) Saving all your Google searches, tied to your identity across devices [1] [2] [30]
2) Reading all your emails. Even if you don’t use Gmail directly, but you’re sending email to someone who does. [5] [6]

3) Saving all your web traffic if the website uses Google Ads, Captchas, or Analytics (and over 85% of all websites use some of their services). Even if you aren’t signed in to a Google account, and you’re using a VPN, they can still use past cookies and browser fingerprinting to identify you. [35] [1] [25] [26]
Google’s reCaptcha fingerprinting includes mouse movements, response time, timezone, screen dimensions, IP address, and any cookies. ReCAPTCHA uses the google.com domain instead of one specific to ReCAPTCHA, which allows Google to receive any cookies you have directly, instead of the website you’re visiting. [35] This concentrates the vast majority of all traffic data in the hands of a single company, which can then be used to de-anonymize users.
4) Everything you do in Google’s Chrome Browser is recorded, including even how long you are idle on a page. [7] [8]

5) Tracking and Saving your physical location, via Android’s GPS and Wifi triangulation. [12] [13]
Even if you turn location features off or set the phone to airplane mode, it still saves your location via Wifi triangulation, which is the process of pinging nearby Wifi hotspots to identify where you are. [9] [10] [11] Wifi triangulation can figure out your real location, even if you have a fake IP address from a VPN. [14]

As intelligence expert and ex-law enforcement Michael Bazzell says, Google is one of the first places law enforcement goes to for information because Androids track everyone’s location so accurately. Bazzell points out that even if you’re not directly involved in something, just owning an Android that was near it, can get you involved in answering police questions. Bazzell’s experience serving in law enforcement and intelligence motivated him to completely cut Google out of his life even though he’s doing “nothing wrong”. [11]
6) Keeping track of who you know to identify new phones or email accounts as you.
Rob Braxman
Privacy expert and phone operating system designer Rob Braxman points out that, by synching everyone’s phones’ contact lists and who they are physically standing near, Google (and therefore governments) can identify unknown devices or email accounts as you. [30] [31] [32a] Braxman further points to publicly available websites made by Google’s Jigsaw division and their partner Moonshot CVE, which openly sells services to governments to track and manipulate search results for targeted users. These users targeted by Jigsaw & Moonshot CVE’s government clients have their search history, location, and identifying fingerprint stored in a database. [32b]
7) Recording and saving audio of your private conversations [16] [17] [18]

Google’s Android has the microphone constantly recording and saving your intimate personal conversations against your wishes for their profit and power. As an extensive academic study of tech patents by Consumer Watch Dog points out, Google will claim this is only to find out if you said the words “Google Assistant,” but yet they have publicly filed patents to scan audio conversations and any available visuals on a variety of home smart devices to identify who is speaking, what you’re interested in, and what you’re doing for the purpose of targeted advertising. [15]

Tracking what you say, what you like, when you sleep, and even when you go the bathroom, goes well beyond Google Assistant helping you do a quick search and would instead be considered an all-inclusive surveillance. [15]
In addition, they’ll allow 3rd party apps to record you without your knowledge because of poor permissions control. As University of California Santa Barbara cybersecurity researchers presented at a BlackHat European conference, 3rd party apps like Silverpush can play high frequency audio, which is invisible to the human ear, on another device like a television ad or mall kiosk. Then your phone’s mic picks up the frequency, to rat out your real identity or location. [34]

Silverpush’s advertising system is embedded into many “free” apps on the Google Play Store. These doctoral researchers warned of the dangers this presents by being connected to wide-spread platforms like Google Ads. To demonstrate this, they played video of their lab experiment, which de-anonymatized a laptop through Tor Browser, because of an Android’s mic next to the laptop’s speakers, which was signed in to a Google account. [34]
Is the Data Sold?

Google has marketing propaganda which claims that they are merely selling advertising space on your devices and not selling the data itself. However, this claim is misleading in a number of ways.
First, not only is advertising sold by demographics or interests, but in addition, Google also allows its advertising customers to target users by name, email, or device ID and reach them almost anywhere. [1] So advertisers can target you specifically and then serve you anything on your specific device by name.

Second, while it’s true that Google technically doesn’t sell your actual name to the advertiser, when your device interacts with an ad, the third party advertiser can easily use your IP address, cross-site cookies, and/or browser fingerprinting to identify you. For example, suppose an advertiser runs an ad for an ebook on how to get out of debt. The advertiser could collect the IP addresses of anyone who clicks it, and so they’d know whose indebted.

“I think the big problem is that we give much more data to Google than it needs,” said Guillaume Chaslot, former Google engineer who worked on YouTube’s recommendations algorithm. [4a] Chaslot’s first-hand experience with Google’s spyware and manipulation inspired him to create the non-group AlgoTransparency.org, which openly says in it’s manifesto, “algorithms don’t have your best interests at mind”. [4b]
Play Store and Chrome Extensions Leak Data

Third, the Google Play Store and their Chrome Browser Extension Store leak application and user data directly to the app’s developers. This is sensitive private information, and these third party app developers are NOT carefully vetted, as almost anyone can put an app in the Google Play or Chrome Extension Store with minimal screening. Examples: [21] [23] [24]
Mental Outlaw
“Mental Outlaw” is a cybersecurity Youtube video influencer who is constantly having his videos about torrents flagged by Google as “dangerous content”. He points out how ridiculous this is because Google does so little to stop real dangerous content. One of the numerous examples he’s given is the Chrome webstore featuring extensions that are malicious hacking malware, which does URL injections to force online shoppers, without their knowledge, to use the malware creator’s affiliate links when they shop online. [22b] These 5 popular extensions got over 1.3 million downloads, which got the attention of McAfee Labs, the research department of the respected anti-virus company.

From McAfee Labs’ articulate research, this is huge security risk because not only is your personal data, like name and location, sent to malicious actors, but the attacker can forward the URL to any site they want. So you might think you’re going BestBuy.com, but it’s really the attacker’s bullshit site to get your credit card info. [22b]

Youtuber Mental Outlaw points out how ludicrous it is that not only did Google allow 1.3 million people to download these extensions, but they have featured status on the Google Chrome store. [22a] And not only does Mental Outlaw find similar malware in the Android Play Store, but Google has changed how apps disclose permissions to remove themselves of liability. Starting in mid-2022, Google has the app developers themselves disclose what permissions the app uses, so Google does not have to do any research. This is a conflict of interest, since app developers are self-reporting what information they get access to, and the end user may not properly be able to evaluate it. [19] [20a]
Sell it via Cookies

Google’s defense to these types of criticisms has always been that they don’t “sell your data” directly. But as laid out in research from the tech-savvy lawyers at the Electronic Frontier Foundation, Google allows advertisers to connect their cookies with Google’s in order to process data on the customer. This process is called “cookie matching” and essentially allows Google to sell the advertiser your information through a cookie. [1]
In the European Union, if Google were caught selling this data directly, it would be illegal. [27] [28] [29] So instead Google finds sneaky work-arounds such as the cookie matching, which allows them to appease the regulators and make statements like “we don’t sell data, we just use the data.” [1]

Conclusion

The more influence that Google has in our society, the more difficult it becomes to avoid their fingerprinting. If every website has a Google Captcha and everyone you talk to demands you talk to them on Gmail, then Google has become the gatekeeper for overseeing all human behavior. They can use this power to influence who sees your messages and what information you are able to find.

By using Gmail or Google Docs, you’re forcing and enabling Google to fingerprint your loved ones or friends. Even if you think you’re doing nothing illegal, you assume that Google will give you and those you care about an equal opportunity for your business to thrive. They can reduce Google’s search traffic to your website, or bounce your emails to potential employers or customers. They can buckle your business at the knees if they think it fits its agenda and by giving them so much information you’ve completely surrendered your freedom.
Well what is their agenda?
In our next article, we’ll discuss Google’s censorship ability to shape society and how affects you.
The Sources for this article can be found here.
Related Articles
Big Tech Abuses Medical Privacy
February 25, 2023 No Comments
In the US, your medical records are protected by HIPAA but your internet medical browsing history on websites like WebMD is NOT. That is the
Read More »
Browser Fingerprints Lead to Price Discrimination
February 25, 2023 No Comments
Some people mistakenly believe they do not need to worry about online privacy because they have “nothing to hide.” In reality, your digital identity expressed
Read More »
Avoid this Monero Vulnerability
February 25, 2023 No Comments
We love Monero. It’s our favorite and number one recommended cryptocurrency. However, it does not offer completely perfect anonymity under all circumstances because there are
Read More »
How to Reduce Google’s Control Over You
February 25, 2023 No Comments
There’s a huge number of steps you can take to reduce Google’s power and influence over your business and personal life. You would get a
Read More »
Google Censors Freedom
February 25, 2023 No Comments
This article presents evidence that Google promotes an agenda of centralized control through systematic censorship on its search, email, video, app store, and ad platforms
Read More »
Session username: Simple / Signal #: +855 68 504 905
Web 3 on IPFS: SimplifiedPrivacy.x
Tor Onion: privacypkybrxebcjicfhgwsb3coatqechwnc5xow4udxwa6jemylmyd.onion
Nostr Public Key: npub14slk4lshtylkrqg9z0dvng09gn58h88frvnax7uga3v0h25szj4qzjt5d6
[email protected] / @Matrix:SimplifiedPrivacy.is
9 notes
·
View notes